A few months back Microsoft announced GA of new advanced security features for Microsoft Authenticator and announced at the same time that in May 2023 they would start rolling out and enable number matching for all authenticator users, now on May 8th, 2023 users will start seeing these new changes, so I want to tell you a bit more about these advanced security features and how to implement them so your end-users can be prepared when threat actors try to use MFA fatigue attack to gain access to users credentials.
But let’s start with some context and answer to the question, Haflidi what is a MFA fatigue attack?
An MFA Fatigue attack is when a threat actor runs a script that attempts to log in with stolen credentials over and over, causing what feels like endless prompts of MFA push requests to be sent to the account’s owner’s mobile device, to keep this up, day and night, to break down the target’s security posture, ultimately, the targets get so overwhelmed that they accidentally click on the “Approve” button or simply accept the MFA request to stop the deluge of notifications they have received.
This type of social engineering technique has proven to be very successful in recent breaches by the Lapsus$ and Yanluowang, e.g. when Uber got breached the threat actors used an MFA fatigue attack, contacted the person pretending to be from Uber IT and told the end-user that he must accept the MFA request to fix some system bug and stop the deluge of requests they were getting.
Now let’s dive into these new advanced authenticator features that hopefully will mitigate and even kill those MFA fatigue attacks.
Number matching is the new feature that will be enforced on all tenants starting from May 8th, 2023.
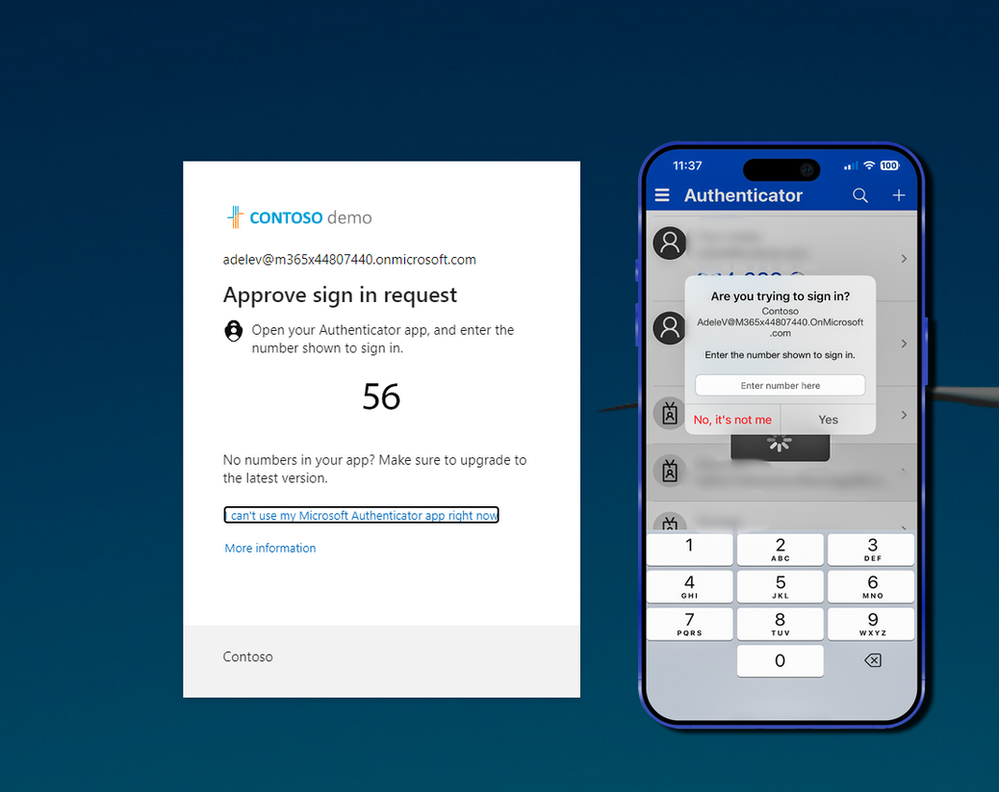
The new number matching feature in Microsoft Entra ID (f.k.a Azure AD) MFA is designed to increase security and reduce accidental approvals, meaning that users will be requested to enter the number displayed on the sign-in screen when approving an MFA request in Authenticator.
If not already enabled, users will now start to get this experience when number matching has been enforced on all tenants after May 8th, 2023.
To enable number matching in the Azure portal before May 8th, 2023, as this UI will be removed, login to Azure Portal and click Security > Authentication methods > Microsoft Authenticator. On the Enable and Target tab, click Yes and All users to enable the policy for everyone or add selected users and groups to enable this for a set of users to begin with, but remember this will be enforced after May 8th, 2023 on all users tenant-wide.
The reason behind number matching is to increase security by preventing accidental approvals and defending against MFA attacks, as the end-user needs to provide the number they see on their screen, within the authenticator, however only having the number matching feature probably solves most of the MFA fatigue attack cases, but I can see this being compromised with social engineering, manipulating the user to pick or write the number that the threat actor in the phone provides to them while pretending to be from IT or something.
However, number matching is only one of the new features in Microsoft Entra ID (f.k.a Azure AD) MFA, other new features include additional context such as location context and application context, and all those features can now be turned on at the same time, providing you more context of where the MFA request is coming from and what application is requesting the MFA prompt, making it easier to detect if the MFA request is legit or not.
What is location context?
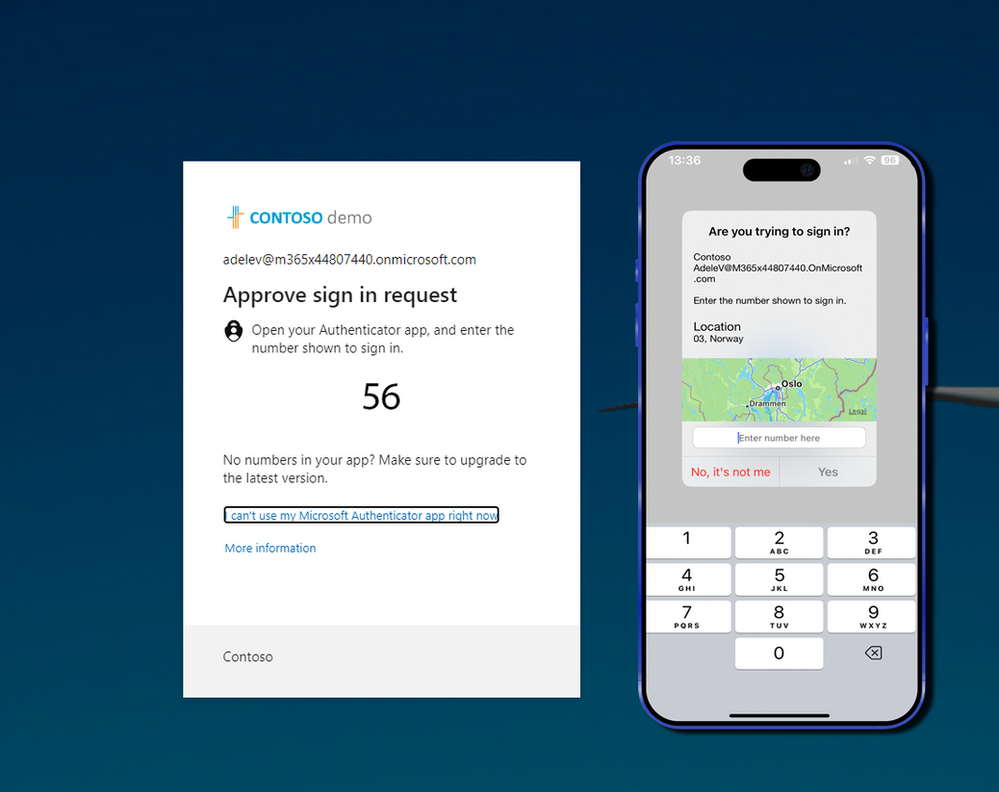
Location context is another new feature in Microsoft Entra ID (f.k.a Azure AD) MFA that allows users to see the geographic location of the device they are signing in from in Authenticator notifications. e.g. you are signing in from your home or remote office you get a geographic location of your home or remote office where you are signing in from, therefore you can be sure that if the sign-in geolocation is from a foreign country it might not be legit and your password might be compromised.
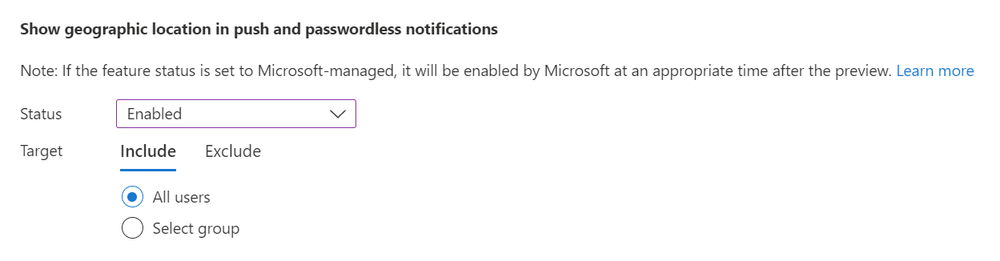
To enable Location context, navigate to Security > Authentication methods > Microsoft Authenticator on the Configure Tab you can toggle the Status of “Show geographic location in push and passwordless notifications” to Enabled, then you can choose to Include All users or select group of users for early adopters, before you enable it for the whole tenant, as of today if you choose Microsoft Managed then this feature is Disabled by default.
After enabling Location Context then the user experience would be like this where users can see the geolocation where the login is coming from.
What is Application context?
The application context is another new feature in Microsoft Entra ID (f.k.a Azure AD) MFA that allows users to see the name of the application they are signing in to in Authenticator notifications. e.g. when signing in from “portal.office.com” you get “Office home” in the Application field in MS Authenticator, this is good to have to be able to see what application is trying to sign in to your account, and it is an additional verification that you are initiating the sign-in your self, but not some bot that uses MS Graph API, PowerShell or such when trying to brute force access to your account.
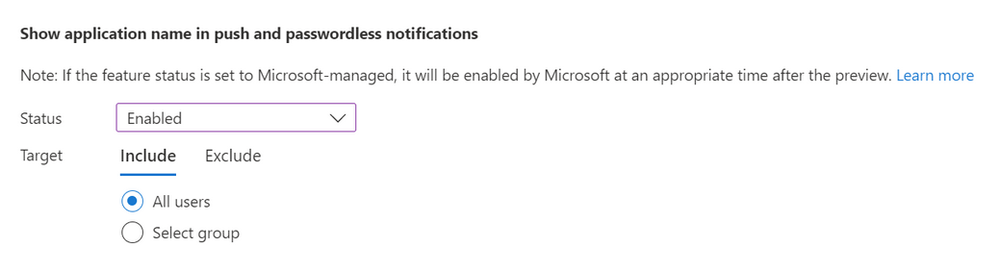
To enable Application context, navigate to Security > Authentication methods > Microsoft Authenticator on the Configure Tab you can toggle the Status of “Show application name in push and passwordless notifications” to Enabled, then you can choose to Include All users or Select groups of users for early adopters, before you enable it for the whole tenant, as of today if you choose Microsoft Managed then this feature is Disabled by default.
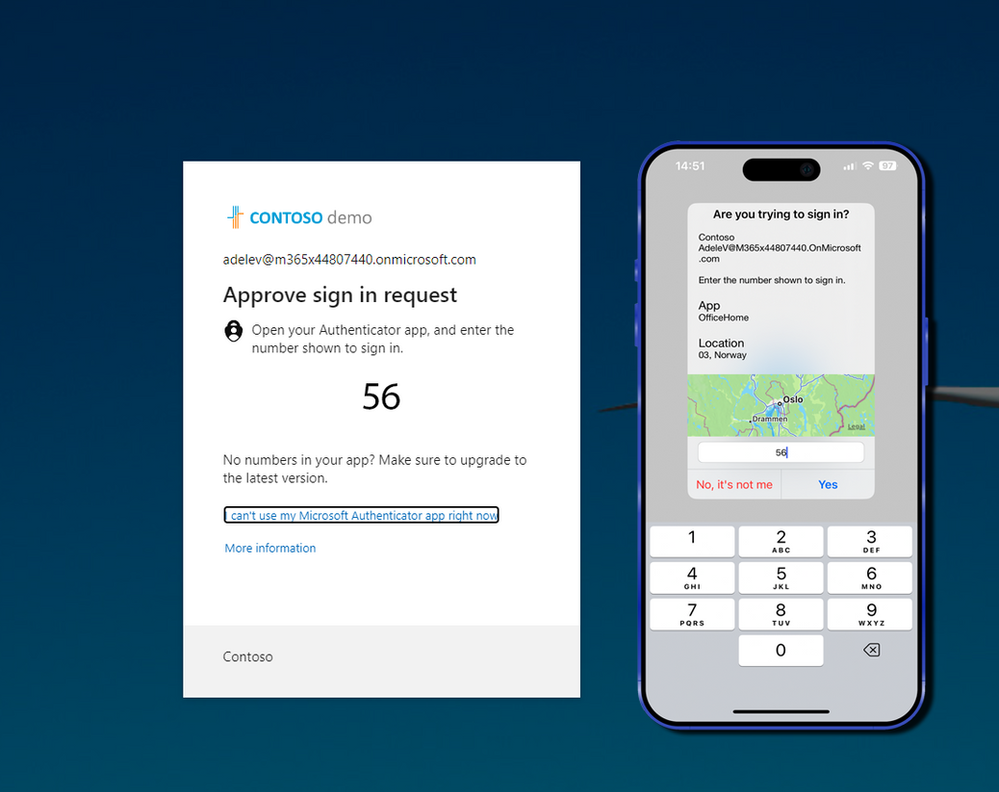
After enabling all advanced features with Number Matching, Location context, and Application context then the user experience would be like in the picture below, where you can see both the application context where the sign-in originated from and what geographic location it’s coming from.
To summarize
Microsoft will enforce number matching on the Microsoft Authenticator after May 8th, 2023, and I highly recommend enabling the other features as well for your users as those features will enhance the security posture and hopefully prevent most of the MFA fatigue attacks.
As always if you liked the post, please hit the like button, leave a comment, and hit that share button to get the information out to as many people as possible, I appreciate your support and wish you a wonderful day.
Discover more from Azureviking | Haflidi's Technical Insights
Subscribe to get the latest posts sent to your email.